
E Tech Group’s Cybersecurity Specialist Matt Smith and Vice President of Business Development Laurie Cavanaugh recently sat down for a candid, in-depth discussion on cybersecurity for the OT network. The webinar, entitled “Fact or Fiction: Debunking Industrial Network Security Myths,” addressed many OT network design and security concerns in addition to discussing the value of an IT/OT assessment.
This article reviews the first three of six myths the automation experts discussed. Follow to our second article for what they covered in the last three prompts.
Automation Fact or Fiction: Cybersecurity Edition, Part I of II
E Tech Group recently hosted a webinar titled “Fact or Fiction: Debunking Industrial Network Security Myths.” Matt Smith and Laurie Cavanaugh of E Tech Group discussed a wide range of topics and strategies regarding OT Network Security. This article reviews the first half of the webinar’s content, including the following topics:
Modern OT network visibility tools can scan OT networks without disrupting operations using both active and passive scanning techniques.
OT Security & Insurance Costs
- Implementing OT security measures can reduce insurance premiums and improve insurability.
Conducting an IT/OT assessment helps identify vulnerabilities and prioritize quick fixes for reassessment by insurance companies.
Ransomware & Emerging Threats
- OT Cybersecurity incidents largely originate from IT systems due to various vulnerabilities.
Common attack vector origins are reviewed.
Non-Disruptive OT Scanning Tools
Fact or Fiction 1: Implementing OT network security changes according to a network design plan can improve cyber insurance costs.
Answer: Fact!
E Tech Group is seeing clients whose insurance costs have skyrocketed, or worse, they are considered uninsurable due to pre-existing risks within their OT facilities. However, upon implementation of a few non-disruptive automated security solutions, they can request a reassessment for insurability and/or a reduction of premium.
Figure 1: Operational considerations make OT security planning and improvement a smart choice for financial and market viability.
Laurie’s Take: Easy Insurance Gains from IT/OT Assessment Fixes and the Need for Ongoing Updates
Implementing OT network security changes according to a well-defined plan can positively impact cyber insurance costs.
Many companies have seen their insurance premiums rise or have even faced becoming uninsurable due to inadequate security within their OT environments. By conducting a comprehensive IT/OT assessment an understanding of the current state of the control system is obtained. By clearly identifying the desired future state, organizations can create a plan that pinpoints key areas for improvement.
Often, impactful changes that enhance security can be made rather quickly once the current state of the system is assessed. By implementing these simple controls solutions, companies can then request a reassessment from insurance providers, often leading to lower premiums or renewed insurability.
However, organizations must demonstrate a commitment to ongoing security improvements, as no system can be entirely secure. As technology evolves, new vulnerabilities may emerge, so regular review and updates to the security plan are required to maintain a favorable insurance status. E Tech Group’s status as a Main Automation Partner allows us to offer ongoing services like these, keeping clients as secure as possible for the long run.
Matt’s Take: Cybersecurity Insurance, Rising Premiums, and Evaluation Criteria
Having an effective OT security management strategy, along with technical solutions that provide network visibility, helps lower insurance costs. It’s important to establish and monitor clear baseline requirements for OT cybersecurity. Doing so allows insurers to accurately assess the organization’s risk and set appropriate coverage or premiums. In addition, it can help organizations identify and reduce silent risks – hidden vulnerabilities that may otherwise go unnoticed. This proactive approach not only minimizes security threats but also contributes to more favorable insurance terms.
Cybersecurity insurance is often viewed as a risk transfer strategy. This risk transfer strategy is steadily being adopted in the OT field. In a worst-case scenario where all cyber-defenses fail, it can be used to cover losses, making it a strategic and important decision for those that have OT networks to protect.
Traditionally, cybersecurity concerns have centered around safeguarding data, with an emphasis on confidentiality and integrity. However, ransomware has become the predominant choice for attacking OT environments. Recent cybersecurity incidents indicate a shift towards ransom demands, business disruptions, harm to reputation, and even physical harm.
A list of sobering statistics includes the following:
- According to Guidehouse insights, electrical utilities saw a 25-30% increase in premiums for cyber insurance in 2022.
- Global cyber insurance markets are predicted to grow from $102 million in 2021 to $442 million by 2030.
OT frequently necessitates separate insurance, requiring organizations to submit an additional OT application even if IT cybersecurity is complete. The European Union Agency for Cybersecurity reported that insurance companies are primarily using questionnaires and site visits to evaluate OT insurance requirements. Questionnaires are noted as the most common means of obtaining information.
Some questions asked by insurance organizations include:
- Do you have an OT security policy that includes cybersecurity?
- Do you maintain a complete and up-to-date OT inventory?
- Do you have anyone that’s primarily responsible for OT cybersecurity?
- Do you have segmentation between OT and IT?
- Do OT environments have direct internet access?
- Is VPN access into your OT environment allowed?
- Do you use multi-factor authentication (MFA) to protect it?
- Do you allow vendors to remote-in to your OT network?
- Do you have defined processes in place for access control?
- Do you have a security operations center (SOC)?
These questions are not new, with most tracing back to NIST Cybersecurity Framework, ISO 27001, and the IEC 62443.
Laurie’s Take 2: Securing Vulnerable Entry Points in the Supply Chain and Beyond
Modern attacks target many different means of entry. As an example, for healthcare providers, a common point of entry is through doctors’ offices. Attackers are hijacking pathways already in place, such as patient portals, accounting, or other natural data transfer mechanisms because often, smaller doctor’s offices are not protected. Likewise, another potential entry pathway includes an unencrypted point-of-sale system.
When E Tech Group works with clients, we look holistically at all communication paths within their supply chain – not only on the automation floor – to make sure that those other data exchange routes are protected.oor – to make sure that those other data exchange routes are protected.
Fact or Fiction 2: Most OT cybersecurity incidents originate from the IT environment.
Answer: Fact!
70% of OT cybersecurity instances originate from the IT environment due to improper network segmentation and shared domain architectures between IT and OT systems.
Matt’s Take: Top Sources of OT Attack Vectors and How IT Vulnerabilities Contribute
IT system vulnerabilities significantly contribute to OT cybersecurity incidents. The high percentage of OT incidents originating from the IT network highlights the necessity for seamless integration of IT and OT security strategies.
According to a 2023 Dragos report, 70% of OT cybersecurity incidents originated from the IT environment. A SANS report from 2023 surveyed 500 companies about OT cybersecurity incidents and identified common initial attack vectors. These included:
- Compromised IT systems allowing threats into OT networks: attacks originating from vulnerabilities in IT systems that spread into OT environments.
- Engineering workstation compromises: unauthorized access to or control over engineering workstations that manage OT systems.
- Exploitation of external remote services: attacks using remote access tools or services (i.e. VPNs, RDP, SSH) to infiltrate a network.
- Exploits of public-facing applications: attacks that target vulnerabilities in internet-accessible software, like websites or APIs, to gain unauthorized access or control.
- Drive-by compromises: attacks that automatically download malware onto a user’s device when they visit a compromised or malicious website.
- Spear phishing with attachments: Targeted email attacks using malicious attachments to trick users into installing malware or divulging sensitive information.
- Internet-accessible devices: attacks on devices connected directly to the internet, such as cameras or IoT devices, often due to weak security measures.
- Compromise of data historians: unauthorized access to databases that store historical process data from OT systems, potentially disrupting operations or exfiltrating data.
- Wireless network compromises: breaches that exploit vulnerabilities in wireless networks to gain unauthorized access to OT systems.
- Supply chain attacks: attacks that target third-party vendors or software used by the organization to introduce malware or exploit vulnerabilities.
- Malware replication through removable media: spreading malware by using infected USB drives or other removable media that are connected to OT systems.
With so many routes into an automation system, an unprepared facility can be attacked from all sides and never see it coming. IT/OT risk assessments are the best place for a facility to start their journey to impenetrable network security.
Laurie’s Take: The Critical Role of IT-OT Collaboration and Lessons from a Case Study in Cyber Defense
There is a strong requirement for IT and OT personnel to collaborate for the purposes of cybersecurity. The following case study highlights the importance of integrated defenses and ongoing vigilance in addressing cybersecurity.
Two years ago, a client experienced a ransomware attack that originated from the IT environment but ultimately affected their OT systems. The attackers likely remained hidden in the IT system for some time before moving laterally to access the OT space. In response, the client collaborated with a director on the E Tech Group cybersecurity design team to develop a strategic plan to strengthen their defenses.
They implemented the plan in phases, prioritizing areas that should be improved first and gradually building up their security posture. Eventually, they were able to deploy a visibility tool in their security automation, allowing much faster detection of and response to active threats.
This proactive approach paid off recently when they faced a second attack. The visibility tool embedded into their control system enabled the client to rapidly identify and neutralize the threat, preventing it from infiltrating the OT environment and avoiding prolonged undetected activity.
Fact or Fiction 3: Visibility/networking topology tools that can actively scan the OT network without disruption do not exist.
Answer: Fiction!
Non-intrusive visibility tools that allow continuous monitoring and detections do exist, and they are crucial for maintaining network security and efficiency.
Laurie’s Take: E Tech Group Vets OT Tools; Provides Feedback to Vendors; NIST on Emerging Threats
While it’s a fact that earlier IT-designed tools were too disruptive for OT networks, critically interrupting normal functioning, newer tools have been developed specifically for OT environments. These OT network-specific visibility tools are designed to operate non-intrusively, allowing for continuous monitoring and threat detection without impacting the stability or performance of essential industrial processes.
E Tech Group does extensive vetting of tools, actively testing them in our lab to ensure they are both effective and suitable for OT environments. When we work with one of our partners in automation technology, we provide feedback that then helps inform their product development.
While quantum computers are not yet being used in cyber-attacks, there is substantial concern that future quantum computers could break current encryption schemes, posing significant cybersecurity risks. This potential has led to proactive efforts in developing quantum-resistant cryptography and understanding the threats that quantum computing could pose.
The National Institute of Standards and Technology (NIST) has already begun evaluating algorithms and cryptography to address these and other emerging cyber threats, which will inevitably stem from newer computation methodologies. E Tech Group’s IT/OT automation professionals will stay on top of new developments to ensure our clients are provided with the best automation security solutions on the market.
Matt’s Take: Modern Scanning Technologies Enable Safe, Active Network Discovery
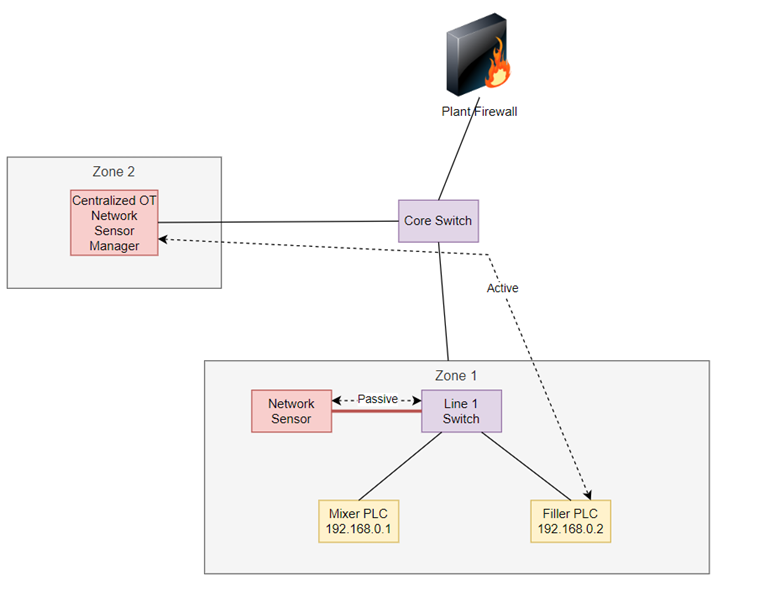
Figure 2: Modern OT scanners use both active and passive scanning for network visibility.
Advanced tools are available that enable precise, non-disruptive scanning while maintaining robust security and operational integrity. Many of these tools combine both passive and active scanning capabilities within a single automation product.
The active scanning capability enhances network visibility by providing deeper insights into network topology. It can gather vulnerability information as well as device configurations, which passive scans alone might miss. The result is better data accuracy.
Modern OT active scanners, such as those by Claroty and Nazomi, are designed to perform active scanning using safe query methodologies to ensure the interaction with a device is non-disruptive. These methodologies include:
- Interacting with devices using native communications supported by the embedded device.
- Traffic shaping to control the timing of data transmission dynamically – based on current network conditions.
- Rate limiting, which involves setting a hard limit of the number of queries to a device over a particular time period to avoid disruption.
- Use of automatic device recognition to tailor active interactions based on each device’s capabilities.
Modern OT active scanning tools perform ICS-optimized discovery, mapping all devices and assets on the OT network. To do so, they employ control packet injection techniques, actively injecting safe, non-disruptive control packets using native OT protocols into the network. The goal is to gather detailed information about each device and its specific configuration to provide insight into existing vulnerabilities.
Quick Thoughts Before Our Digital Intermission…
We are deep into the age of automation. Between the digital transformation, the advent of industrial AI, and the capabilities of hackers to deploy sophisticated attacks on OT, companies who don’t prioritize taking the offensive on their network security carry catastrophic risks.
Whether the cost of a cyberattack is lost revenue, data, IP, operations, or anything else, the cost to reputation and viability can be even higher than those sky-high insurance premiums. E Tech Group’s team is here to help with education and experience in this new frontier of automation security. We stand ready as a resource, whether you’re preparing for the worst with one of our IT/OT Risk Assessments, or responding to it with our emergency disaster recovery services.
Get to know the authors:
Matt Smith, CISSP is a Cybersecurity Specialist with 10 years of experience in automation and technology focused on protecting critical infrastructure, industrial processes, and operational technology. He develops and implements tailored cybersecurity strategies to ensure OT systems are secure, resilient, and optimized for their unique challenges.
Laurie Cavanaugh is the Vice President of business development for E Tech Group. She has more than 35 years of experience in the automation and technology industry. Laurie engages with clients using a partnership approach to help them further develop their businesses through advancements in automation, control, and intelligence solutions.
Speak with an Expert
Reach out to us here and someone will respond within 24 hours.
"*" indicates required fields
