
This article addresses material covered in the second half of the E Tech Group webinar, “Fact or Fiction: Debunking Industrial Network Security Myths,” where E Tech Group’s Matt Smith and Laurie Cavanaugh addressed many OT network design and security concerns and the value of an IT/OT assessment. For a review of the first half of the webinar, visit the previous article.
Automation Fact or Fiction: Cybersecurity Edition, Part II of II
E Tech Group recently hosted a webinar titled “Fact or Fiction: Debunking Industrial Network Security Myths.” Presenters Matt Smith and Laurie Cavanaugh discussed a wide range of topics and strategies with regards to OT Network Security. This article reviews the second half of the webinar’s content, including the following topics:
- Protecting Legacy OT Assets
- There are several effective strategies to protect legacy control system assets until they can be replaced, including network segmentation, isolation, and cloaking.
- Regular patching and prioritization of legacy upgrades are crucial for ongoing security.
- Low-Impact Security Measures
- IT/OT security measures can be implemented cost-effectively with minimal production impact using incremental strategies.
- Passive and active scanning tools, network meshing, and single-pane-of-glass solutions all offer non-disruptive visibility and security.
- Assessment workshops help organizations prioritize security needs and phase implementation to avoid costly downtime while balancing functionality and budget.
- Scalable Network Design and Future-Proofing
- OT networks should be designed with future growth in mind, ideally with additional capacity to avoid costly redesigns.
- Early collaboration between IT and OT teams is critical to ensure network designs can handle future expansions to an automation system, including production shifts and new equipment, balancing cybersecurity with operational needs.
Fact or Fiction 4: : Legacy OT assets cannot be effectively protected so immediate replacement is the only way to ensure cybersecurity protection and risk avoidance.
Answer: Fiction!
Legacy systems can be protected and do not inherently present a network security risk.
Laurie’s Take: There are effective Solutions for Protecting Legacy OT Assets Before Their Replacement
Many clients have OT assets at various stages in their lifecycle, including control systems that are entirely obsolete. In addition, it’s common for products that are still in their active lifecycle to be out of date with patches, often because the process to install updates is so disruptive to operations.
There are several types of tools available to protect these vulnerable automation assets, including scanning and visibility tools, but also cloaking technologies. Cloaking technology works by making assets invisible on the network. One of our automation software partners, Opscura, has a cloaking digital segmentation technology that can be implemented very quickly. By doing so, we buy further time to address the vulnerability issues in a more permanent manner, making it an important part of a multilayered security solution.
Regardless, regular control system upgrades and patch solutions are still necessary for maintaining a secure network. To that end, it’s important to make a plan for the upgrades to occur based on their relative priority and downtime availability.
When we work with a client, one of our goals is to create a comprehensive IT/OT inventory and schedule remediation tasks based on their relative priority. Collaboration between all stakeholders is critical to balancing the remediation process with ongoing protection. We facilitate this process by identifying the ways that a client can accomplish upgrade work in parallel with maintaining a secure network.
Matt’s Take: Practical Strategies for Securing Legacy OT Assets Until Replacement
While immediate replacement of legacy OT assets is ideal for reducing risks, it’s often not immediately feasible. The following are effective strategies to protect legacy assets until they can be replaced:
A variety of tools protect against unauthorized access, including user-based access control as well as behavior analysis tools.
Recovery planning: A robust incident response plan helps ensure readiness to effectively address any risk or threat associated with these legacy assets.
Network segmentation: By dividing the network into a smaller section for these legacy assets, any breach is prevented from spreading to other parts of the network.
Network isolation: By separating these assets from the rest of the network, communications are restricted to and from the broader network, except under tightly controlled, specific conditions.
Opscura: This tool provides cloaking mechanisms to mask legacy assets without needing to re-IP the entire network. These tools can be placed into a flat network and can mask legacy assets behind a firewall sitting at [Purdue] layer 2.
Enhanced monitoring tools help detect real-time anomalies.
Patch management keeps legacy control systems updated, although it is often not an option for legacy assets due to obsolescence.
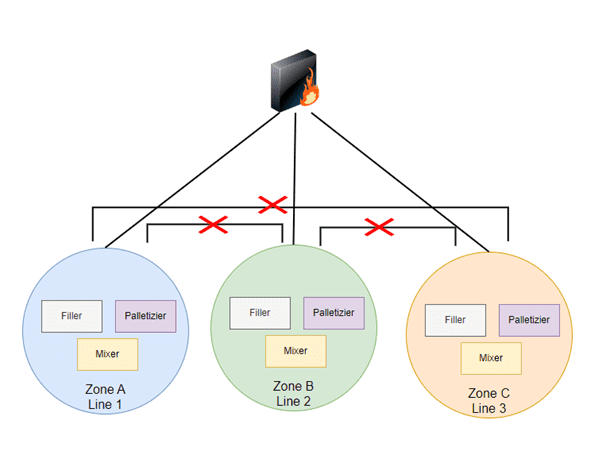
Figure 3: Network segmentation prevents a threat from traversing throughout the facility.
Fact or Fiction 5: Implementing IT/OT security measures is always
expensive and requires extensive production downtime
Answer: Fiction!
Many security measures can be implemented with minimal disruption to production processes.
Laurie’s Take: IT/OT Assessment Workshops Lead to a Balanced Plan
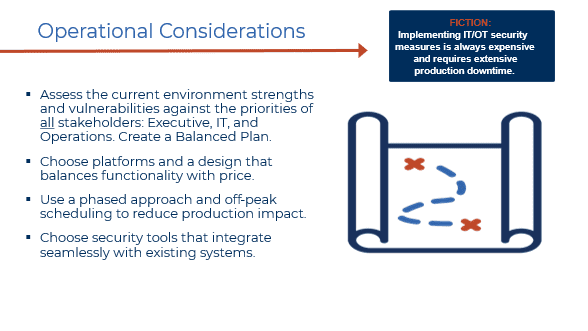
Figure 4: Strategies for implementation of robust OT network security measures.
Developing a robust plan for addressing cybersecurity is foundational to the process of fully addressing the potential threat of an attack. The plan should include the prioritization of security measures as determined by key stakeholders, including IT and OT personnel, executives and even shareholders (for a publicly traded company).
Publicly-traded companies must disclose breaches when they occur, and the first thing that shareholders, the insurance company, or other decision makers will be looking for is a strategic, well-thought-out cybersecurity plan that protects every corner of a facility’s automation systems.
Creating this kind of balanced plan involves all stakeholders weighing variables like asset vulnerability and criticality to revenue. For example, critical OT assets that generate revenue may need more protection than outdated, less critical systems that don’t run as often.
During our IT/OT assessment workshops with clients, we help them with the following:
- Creating a plan as described above.
- Selecting appropriate tools and platforms that balance functionality with price. Several tools have overlapping features so we help clients obtain the most functionality that addresses their needs and budget.
- Creating a thoughtful phased implementation plan to manage costs and minimize disruption. In the case study discussed in Part I, Question 2, the client had been addressing cybersecurity with a phased approach over a two-year period.
- Selecting security tools with consideration for staff familiarity with current platforms.
Finally, one of our automation software partner’s tools can analyze PLC programs and find all referenced devices within the ladder logic. This tool is particularly useful in the planning phase, as it helps uncover shared assets that may be used concurrently by multiple lines, machines, or panels that may otherwise have gone unnoticed.
Matt’s Take: Low-Impact IT/OT Security Options – Scanning Tools, Network Meshing, and Single-Pane-of-Glass Solutions
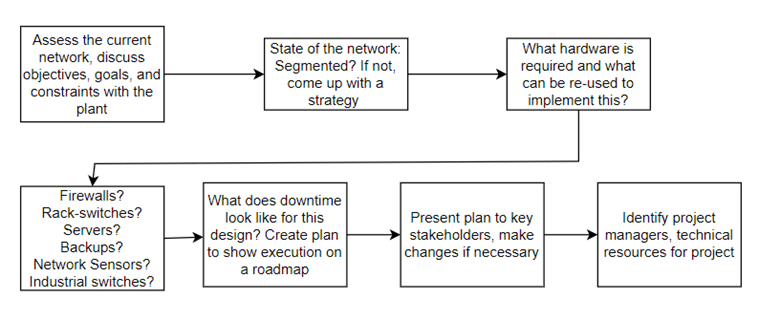
Figure 5: A roadmap for addressing cybersecurity concerns
It’s a misconception that IT/OT security measures are always costly and involve significant downtime. In reality, many security solutions are cost-effective and can be integrated with minimal production impact. As Laurie mentioned, using an incremental implementation strategy can also help with both cost and downtime concerns.
There are a variety of low impact, non-intrusive technologies that can be used to obtain necessary information about the overall automation system. These include passive scanning tools, as well as the active scanning tools specifically designed for the OT environment described earlier.
Vendor solutions today often include the meshing of network equipment, which creates an interconnected system of network devices that communicate across multiple pathways. Meshing enhances network resilience, reduces single points of failure, and improves segmentation, containing potential cybersecurity threats to isolated areas.
Additionally, many vendors offer single-pane-of-glass solutions. These solutions have a unified interface providing visibility into network and security operations, allowing administrators to monitor all devices, data flows, and security alerts from a single dashboard, therefore improving threat detection and response time.
These solutions not only provide the option for scalability across multiple plants—ensuring consistent cybersecurity protocols across locations—but also offer security enhancements that are both cost-effective and minimally disruptive to production.
Fact or Fiction 6: An OT network design should tie back to corporate
priorities and balance efficient traffic flow and strong cybersecurity against the cost and timing of installation.
Answer: Fact!
Effective network design can ensure sensors are strategically placed to maximize visibility while minimizing costs.
Laurie’s Take: Prioritizing Stakeholder Involvement, Disaster Recovery, and Balancing OT Security with Operations
As described earlier, it cannot be overstated how important it is to ensure that all stakeholders are actively involved in the planning and design of OT network security strategies. Reiterating, an organization must always be prepared to answer questions from insurance companies, boards, and shareholders alike about their priorities, plans, and current progress with respect to cybersecurity. To that end, small steps forward are always better than no steps taken at all.
In addition, even for organizations that feel they have a cybersecurity plan in place, it never hurts to bring in an external team for a fresh perspective. A common observation our team has made is that there seems to be a general absence of cybersecurity disaster recovery planning for OT assets. This scenario should be fully addressed, just like a natural disaster scenario generally has a plan.
While a ransomware attack is very similar to a natural disaster in terms of operational disruption, because there isn’t physical site damage, there are many effective ways to plan for the recovery from this type of disruption. E Tech Group offers continuous emergency response, disaster planning and recovery services that offer automation solutions before, during and after such an event.
Cybersecurity policies and procedures should be in place, but they should also be reviewed and actively tested on a regular basis to ensure they remain effective. Finally, it’s important to balance cybersecurity efforts with operational needs, as too much restriction can hinder data flow and other efforts to improve the facility’s operation.
Matt’s Take: Aligning OT Network Design with Business Priorities, Future Growth, and Security
Design of OT networks should align with corporate priorities, supporting overall business objectives and strategic goals. While robust security measures should be incorporated, operational integrity must also be maintained as it’s critical to system performance. Likewise, security and performance needs must be balanced with budget constraints and available project timelines.
In addition, design the network to accommodate future growth and changes to the control system without requiring significant redesigns later. By including extra capacity, such as adding 20% more network ports than are currently in use, organizations can create long-lasting networks that require minimal changes over time, ultimately helping to control future costs.
Laurie’s Take 2: Consider the Network When Planning for Line and Equipment Changes
With respect to network design and scalability, keep in mind that future changes such as consolidations or moving production lines can significantly impact network design. To that end, it’s important for IT and OT teams to get involved early in the planning process. Some issues that can arise as equipment is moved includes the need to reassess segmentation setups.
In addition, the overall load on the network may be impacted, particularly in the case where new equipment with greater data capabilities is going to be installed using native OT protocols. The goal is to gather detailed information about each device and its specific configuration to provide insight into existing vulnerabilities.
Closing Remarks on the Costs of Lagging on OT Cybersecurity
In the age of automation, nothing is safe. Rapid developments in technology are always matched by rapid developments in hacker capabilities, and a particularly sophisticated attack can bring down an otherwise unshakable company. The cost of implementing robust, advanced protocols for OT networks is critical to limiting exposure to these very real risks, and to keeping those insurance premiums low.
E Tech Group leverages hundreds of talented engineers, decades of experience, a depth of expertise across sectors, and a drive to create the most strategic, secure automation solutions available to offer clients the best automation and control solutions, always customized to your current needs and future goals.
Get to know the authors:
Matt Smith is a Cybersecurity Specialist with 10 years of experience in automation and technology focused on protecting critical infrastructure, industrial processes, and operational technology. He develops and implements tailored cybersecurity strategies to ensure OT systems are secure, resilient, and optimized for the unique challenges.
Laurie Cavanaugh is the Vice President of Business Development for E Tech Group. She has more than 35 years of experience in the automation and technology industry. Laurie engages with clients using a partnership approach to help them further develop their businesses through advancements in automation control and intelligence solutions.
Speak with an Expert
Reach out to us here and someone will respond within 24 hours.
"*" indicates required fields
