
You start your day as you normally would, reaching for your cell phone complete your morning routine. Maybe you check your bank account, the weather, the score from last night’s game. You do all of these things through apps that don’t function within a uniform operating system and allow for the security of password protection, ensuring firmware and protocols are up to date, or facial recognition.
You may have to utilize different browsers because your banking website doesn’t function optimally with your default. What happens if the browser you used or sites you visited aren’t protected? You’ve just opened yourself up for and become vulnerable to malware or ransomware attacks, which could have negative financial and personal repercussions.
Your phone itself could be an old model that is no longer supported by the manufacturer, preventing new security patches to be released for it while external threats continue to evolve.
Now, imagine this on a large scale within a production or manufacturing facility managing numerous disparate systems, some may be on the local or secured network, some may not be. You can’t see at scale what may or may not be performing optimally, what’s nearing end of life or what may potentially be corrupted without physically walking or auditing your site every time you need this information. This not only impacts your facility, but employees, clients and potentially shareholders. What if there was something you could do? A way to proactively evaluate, align, and remediate potential threats, out of date protocols, and aging hardware. That is what an IT/OT Vulnerability Assessment makes possible.
What Exactly is an IT/OT Vulnerability Assessment?
Before you start, it’s important to have an intimate understanding and familiarity with your facility that will help in contextualizing the purpose behind an IT/OT Vulnerability Assessment. The IT, OT, Operations and Corporate level members should be aligned in understanding why they are wanting/needing this assessment to ensure communication remains open and information is digestible from the top down.
In its simplest terms, this multi-point assessment involves a digital and physical audit of your site to compile a full aggregate report of asset inventory, if it does or does not live on your network, what networks the system is comprised of and whether or not they’re secure. Once the assessment is complete, it’s used to develop a recommended remediation plan to improve the IT and OT infrastructure that operates in your facility.
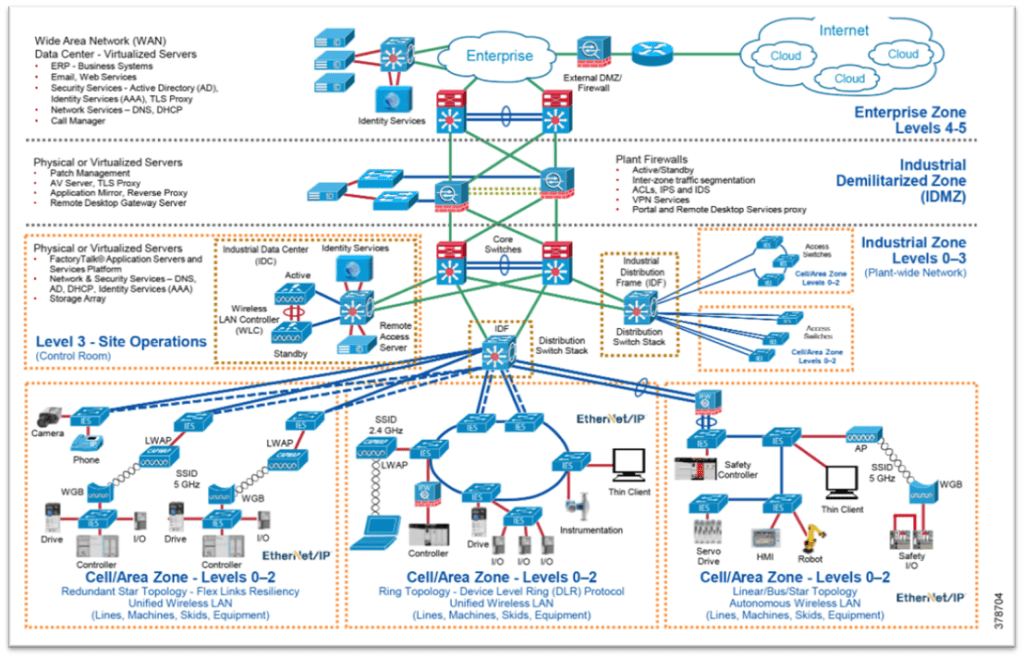
During the physical, on-site portion of the audit, a group of network engineers typically walk the site with operations team members to take pictures of and document all assets living within the control panels, noting if this mimics plant drawings and documented layout.
The digital portion consists mainly of granted VPN access and the use of a scanning tool allowing the network engineer to assess network health and security and identify where, how, and if assets are on the network topology.
Once complete, all of this information is rolled up into a report that will be presented and digested from the corporate level down. From here, a plan for remediation can be created and deployed ensuring anything that may be at risk or near end of life can be proactively remedied before inevitable failure and impacted profitability.
How Could an IT/OT Vulnerability Assessment Help My Facility?
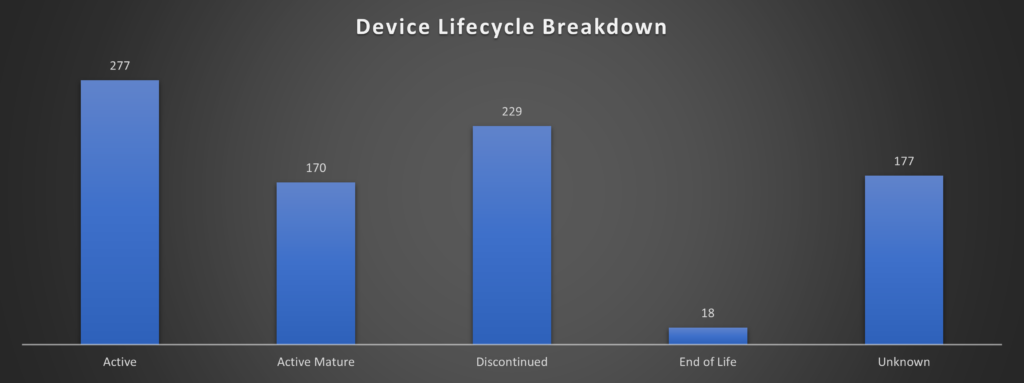
The goal of the assessment is to provide a detailed view into your IT and OT networks to help determine what might be at risk, what is near end of life or already compromised. Allowing for the facility to work proactively instead of reactively, maximizing throughput.
There are numerous use cases where an IT/OT vulnerability assessment could help your facility. Whether it’s software or hardware, they’re both susceptible to failure which will impact your bottom line. Understanding how they’re impacted both individually and together helps emphasize the need for maintaining and protecting these systems.
If you haven’t taken the precautions necessary to secure your IT network, you’ve left your facility open to the potential of malicious threats, manifesting themselves in the form of malware or ransomware. These can continue to negatively impact not only your facility’s security, but trickle down into the insurance policy, which in some cases can mean millions of dollars. Not taking the steps to ensure all the protocols listed on your policy are followed or actively remediating identified threats could have you labeled a liability. That not only affects your facility, as you can see premiums increase while coverage decreases, but if you’re publicly traded, it could eventually impact your shareholders. Having an assessment can help ensure everything listed on your policy is accurate and being upheld, potentially leading to lower premiums and increased coverage, all while protecting your stakeholder interests.
Protecting your physical assets can be a large challenge in and of itself. Understanding every component is repetitively performing its own task, it’s imperative that they’re doing this optimally and efficiently. As these pieces age, efficiency declines and eventual repair or replacement is unavoidable. An assessment can provide a plan to remediate those disparate systems living on separate networks or no network at all. Having the ability to use real time analytics to help identify when these components start to degrade allows for the utilization of predictive maintenance to schedule downtime when it’s least likely to impact production and profitability.
Knowing how critical it is to secure and maintain the working relationship between IT and OT, an IT/OT Vulnerability Assessment can be the first step in helping remediate any items near end of life or at risk in your facility; providing the opportunity to optimize performance, output, and revenue.
Begin Your Journey to Industry 4.0
Download our Beginner’s Guide to IT/OT Assessments to gain an understanding of what an IT/OT Assessment is, its benefits, and how to get started today.
