In the second edition of this two-part series on OT network security, the popular term “Zero Trust architecture” is fully broken down into individual devices that together take both an offensive and defensive approach to securing an OT network.
Zero Trust Architecture: An All-Encompassing Term for a Defensible OT Network
While the term “zero trust” has become popular within the field of operational technology (OT) network security, its meaning stems from the evolution of ever-increasing network security measures that have had to be implemented in response to increasingly complex threats. As the threat frequency and sophistication of a breach has increased, security measures have also had to increase in lockstep, assuming less and less trust for devices operating on the network.
At this point in time, the most robust network design always assumes the worst – trusting absolutely nothing attempting to access an OT network until full authentication has occurred, and regularly interrogating devices currently on the network as if they’ve become malicious. Trust no device, at any point in time – zero trust. Simply put, when it comes to cybersecurity, you’ll find safety in skepticism.
Zero Trust vs Safe Zones: Why Assuming the Worst is Best
In the Zero Trust model, full identification and credentialing occurs on a continual basis for every single device attempting to access the network. Traffic monitoring is continual, access is limited, and no safe perimeter is assumed.
This is a different, nearly inverse approach than that traditionally implemented within an IT network, which assumes a “safe zone” and primarily defends that zone at its perimeter. The Zero Trust approach requires a collection of network components and software solutions, each doing their own task, that work together to collectively keep the network secure.
Some components monitor data; some log events; some actively interrogate existing devices using the network to authenticate themselves and prove their credentials; another provides “backdoor” access to the network – a needed gateway in the event of a network failure.
The combined effect of all these devices is that the network is secured through both offensive and defensive techniques. This “trust no one” approach to OT network architecture ensures (1) your system is ready to defend against breaches, and (2) your system is ready to respond to and fight a breach.
This is superior to the traditional approach to IT security, which only considers (2) in its logic. Why is this strategy obsolete? Because we are no longer dealing with known, finite types and scopes of cyberattacks. Our approach to security needs to be as creative and aggressive as the bad actors attempting to compromise your network.
OT Zero Trust: Core Concepts of the Maturity Model
Zero Trust as a security paradigm is centered on data or resource protection and is based on the idea that trust should never be taken for granted and must always be assessed.
According to the Zero Trust Maturity Model, a zero trust strategy is made up of 5 pillars:
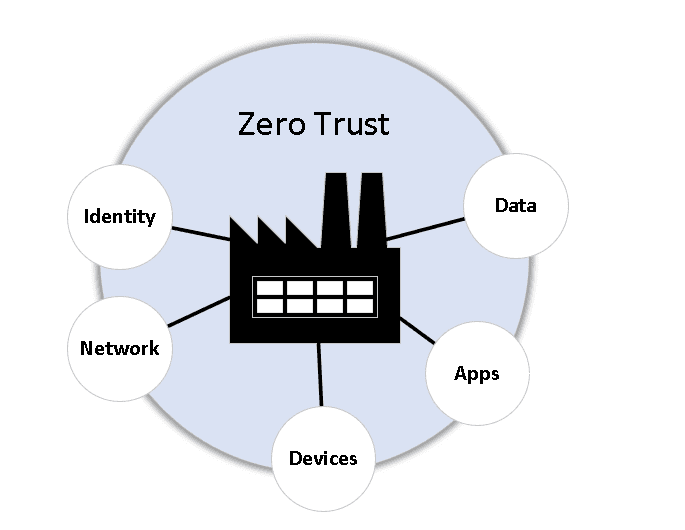
- Identity
- Devices
- Networks
- Applications and Workloads
- Data.
An end-to-end strategy for protecting corporate resources and data, Zero Trust architecture covers identity (both human and non-human entities), credentials, operations, endpoints, hosting environments, and the network infrastructure. Limiting access to resources to those who truly need them and only granting the bare minimum of rights (read, write, and delete, for example) will help ensure that the mission is completed.
While there are variations on the zero trust strategies one could effectively utilize, an effective OT Zero Trust implementation should be closely aligned to the CISA Zero Trust Maturity Model.
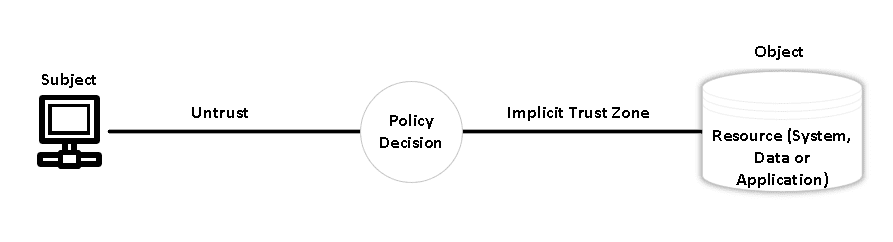
No Implicit Trust: Validate Every User & Every Device
This fundamental shift in perspective ensures that trust is earned, not assumed, as each user and device undergo thorough validation on a continual basis. Following an initial IT/OT Assessment, the spotlight turns to validating every interaction within the operational ecosystem.
With the aid of advanced tools and protocols, system integrators meticulously authenticate users and devices, leaving no room for unauthorized access. By enforcing rigorous validation at every step, organizations fortify their digital landscape against potential threats, ensuring a secure and resilient operational environment.
The main objective of this definition is to prevent unauthorized access to data and services while enforcing access control at the most granular level feasible. In other words, only subjects who have been granted permission (a user, application, or service, and device) can access the data, excluding all other subjects (i.e. attackers).
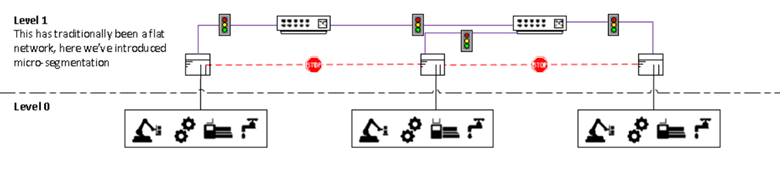
Microsegmentation: Transition From a Flat Network to a Zero Trust Network
Microsegmentation is a strategic approach to network security in operational technology (OT) environments that aims to improve protection and control by dividing the network into smaller, isolated segments. Segmentation intends to protect the entire network by ensuring that a breach in one place doesn’t necessarily compromise the entirety of the network.
OT microsegmentation is closely aligned with the Zero Trust model because it implements granular access controls and segmentation policies within operational technology environments, enforcing the principle of least privilege and reducing the attack surface, thereby improving overall security posture.
The Purdue Reference Model and the ISA 62443 Design are both appropriate frameworks for this project:
The Purdue Reference Model is a hierarchical framework that classifies network communication into five levels. The model allows for the implementation of OT security measures in an automated manufacturing network environment. The highest levels (four and five) are associated with management-related data flow and connectivity. Level 5 connects the network to the outside world.
In contrast, level 0 is where local production devices communicate with one another during normal operations. Northbound/southbound traffic refers to network traffic that moves up or down a level, whereas eastbound/westbound traffic refers to traffic that remains on the same level.
ISA 62443 Design isn’t exactly a model so much as it is a series of standards and best practices developed jointly by the International Society of Automation (ISA) and the International Electrotechnical Commission (IEC) focusing on cybersecurity for industrial automation and control systems.
The theory of the ISA Design is rooted in layered security measures, a deep defensive approach, network segmentation, and secure development life cycle (SDL), under a comprehensive risk-based approach. These standards provide a comprehensive framework to help organizations improve the security of their critical infrastructure.
Strategize Your Future: An IT/OT Assessment Supports the Planning Phase
Automating the discovery of OT network inventory and mapping is the first technical step in the assessment process. Defining and laying out the devices on the system begins the process of securing the network. While a variety of tools and strategies can be used to complete this type of inventory of devices, an IT/OT assessment, commonly completed by an automation system integrator, will provide this full description and network layout as it currently exists.
To perform this analysis, a system integrator may use passive or smart polling software for discovering asset data as well as network infrastructure monitoring use cases. While connected to the network, this software will determine all the connectivity within the network and generate an asset inventory list with firmware, IP address, make/model data including a topology diagram of the data connections of everything that uses the network to communicate.
Identify Asset Values: The Crown Jewel Analysis
Following the initial steps of an assessment, the next critical phase entails performing a crown jewel analysis. This analysis focuses on identifying and prioritizing the most critical assets in the operational environment. These assets, referred to as “crown jewels,” serve as the backbone of industrial operations and must be protected at all costs.
Control system integrators can use automated discovery tools and strategies, such as passive or smart polling software, to meticulously map out the OT network infrastructure and compile a detailed asset inventory. This inventory includes critical information such as firmware details, IP addresses and device models, as well as a comprehensive topology diagram that depicts data connections.
With this understanding, organizations can strategically fortify their crown jewels against potential cyber threats, ensuring the resilience and security of their operational infrastructure.
Ensure Remote Access is Secure: MFA/PAM
In fortifying remote access mechanisms within OT networks, organizations can enhance security through the adoption of Multi-Factor Authentication (MFA) and Privileged Access Management (PAM) solutions. MFA provides an added layer of security by necessitating users to authenticate using multiple factors like passwords, biometrics, or security tokens, thereby mitigating the risk of unauthorized access. Concurrently, PAM solutions play a vital role in upholding the principle of least privilege, granting access solely to authorized users and limiting their permissions based on predefined roles. By integrating MFA and PAM into remote access designs, organizations bolster their security posture, ensuring stringent control over access to critical OT systems and safeguarding against potential threats.
Ongoing Monitoring & Visibility: OT Threat Hunting
When an event occurs within the OT network, this information must be logged, analyzed, and potentially acted upon. This is the job of the Security Information and Event Management (SIEM) system in combination with a Security Operations Center (which is often cloud based). Together, they serve as the central hub of the organization’s cybersecurity strategy, keeping track of events and anomalies within the system and then acting upon any detected threats.
The job of a threat hunting engine, usually situated at level 3 on the OT network, is to proactively monitor for malicious data that could be a security threat traveling on the network. Recall that the Zero Trust strategy assumes any device, at any time, can become malicious. In general, this type of engine will create hypotheses based on available normal data patterns within the network, as well as knowledge of current threat intelligence. From there, those hypotheses will be investigated by the engine to detect and then address potential security threats.
As an example, a threat hunting engine will constantly interrogate devices on the network for their credentials and compare them with those of known OT assets. Only known assets are permitted to communicate on the network, within their specifically allocated security level. In addition, a threat hunting engine will scan for known OT/ICS specific threats. To robustly secure an OT network, all levels, and directions of traffic within the Purdue model must be monitored, as if an attack has already occurred, to reduce its reach.
Remain in Operation Amidst an Attack
The concept of Zero Trust architecture has become critical to securing operational technology (OT) networks. As cyber threats continue to evolve, companies must take a proactive approach that trusts nothing and always assumes the worst. This approach involves continuous identification, authentication, and monitoring of devices on the network. To implement Zero Trust, it’s essential to start with an IT/OT assessment to understand the network’s layout.
In an era of increasing cyber threats, the possibility of an attack must not be considered as an if, but as a when. With a fully implemented zero trust environment, the breadth and reach of an attack vector is reduced to only the device that has been breached. The result is that the plant remains in operation during an attack and the remediation process – a best case scenario for an otherwise devastating event.
Part 1 of this series on cybersecurity in industrial automation, “The Case for Investing in Cybersecurity”, we discussed the integral role of OT security in preventing and mitigating cyberattacks in the era of digital transformation.
Click Below to read Part One of this blog series
Learn more about our cybersecurity expertise
If you’re interested in implementing a zero-trust architecture at your facility, complete the form and we will be in touch to see how we can help.
Begin Your Journey to Industry 4.0
Download our Beginner’s Guide to IT/OT Assessments to gain an understanding of what an IT/OT Assessment is, its benefits, and how to get started today.