
In an era of increased frequency and sophistication of cyber threats, any one defensive approach can be hacked. To be fully guarded, a secured network must incorporate several different components.
A cyberattack on an exposed OT network is a looming security risk with potentially devastating consequences, including extended production downtime, system reformatting and possible hardware replacement. The costs of a cyberattack can be financially catastrophic, but can also hurt your reputation or cause compliance issues that result in hefty fines and even shutdowns.
Part 1 of this 2-part blog series helps the reader to understand both the challenge of securing a network as well as the urgent need to do so. Part 2 of the series will discuss most of the OT network components and structuring strategies that collectively build a Zero Trust network architecture.
Cyberattacks are a reality; no one can avoid them forever. The goal is to be sufficiently resilient to remain in operation in the midst of an attack. And to accomplish that, we must understand the whats, whys and hows of industrial security automation.
Understanding the OT Network in an Automated Facility
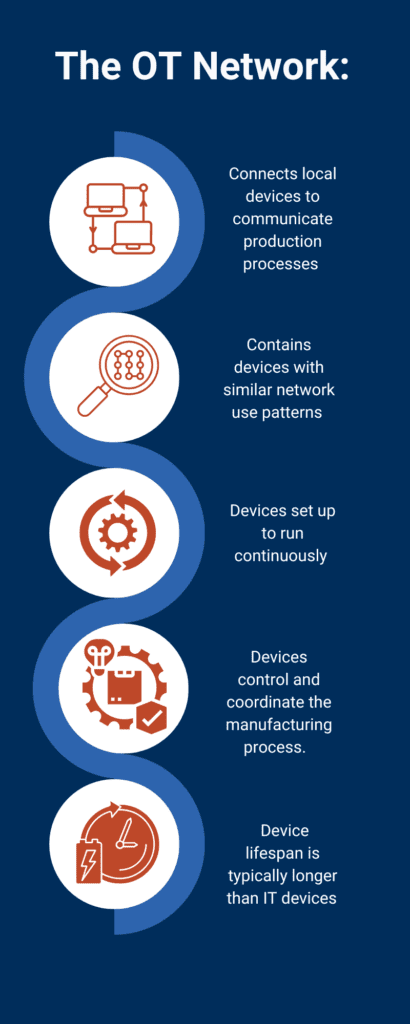
The Operational Technology (OT) space on a plant floor is a highly complex network environment with distinct characteristics from its Information Technology (IT) network cousin. The space has traditionally been used in a limited manner, connecting local devices that communicate with each other for production purposes and little else.
While these devices may be of varying ages and vulnerabilities, as a group their network use patterns are similar, and distinct from typical IT network traffic. Devices on an OT network are generally setup to run all the time, requiring very reliable, and continuous communication as they control and coordinate the manufacturing process.
The lifespan of OT devices is typically longer than IT devices, which means that supporting legacy and aging devices is often a requirement. This requires a system integrator adept not only at complex automation solutions, but at integrating security concerns into those solutions.
Greater Data Visibility Comes with the Increased Risk of a Cyber Attack
In recent years, there has been a push for greater data connectivity and visibility from the production floor all the way to management. This need defines digital transformation – data originating from the production floor now has destinations much further away than those locally connected devices. OT data is now used to:
- -Analyze efficiencies, look for weaknesses and bottlenecks in production flow.
- -Provide better insight for business decisions.
- -Administer to the demand for external data, such as firmware upgrades to find its way to manufacturing equipment.
This change in data use pattern requires the joining of the OT and IT Network within a production environment. To accommodate this evolution, the OT network breadth and visibility has expanded. With it comes the increased exposure to potential cyber threats targeting all types of connected manufacturing equipment. Without the right IT/OT automation solutions, the advantages of greater data visibility can be rendered null by the fallout from a single cyberattack.
Cost vs Risk Management: Making the Case for Cybersecurity
Cybercriminals have been increasingly targeting the manufacturing sector for the past several years. The growth of data compromise within this sector is staggering, moving from 70 attacks in 2020, to 222 in 2021, to 249 in 2022. Between 2019 and 2023, the average cost of a data breach in the industrial manufacturing industry was found to be approximately 4.5 million dollars.
That means, on average, a single cyberattack will cause a company to bleed out nearly $5 million dollars virtually overnight. For small and medium-sized entities, this can be the difference between sinking and swimming in their market.
Ransomware attacks are the most common breaches we encounter in the industrial automation services industry. When a breach is successful, attackers will demand money in exchange for returned data. With no proven track record, the victim company is then forced to make the difficult decision of either paying off the criminals in the hopes that their data will be returned, or leaving it all behind and rebuilding from the attack. Both are difficult, expensive options with severe consequences.
Asking the Right Questions: How Potentially Catastrophic is a Cyberattack?
The case for securing an OT Network within a production environment can be considered by asking oneself the following questions:
1. If a ransomware attack occurred tomorrow and compromised all backups, how much of a problem is that for you?
This question isn’t as simple as it may at first seem, because a breach of your automated systems can affect every aspect of your business – in and out of the facility. You’ve got to consider:
- How much critical data would be lost? Is it easily recreated, or irreplaceable?
- How would a data breach or service disruption impact customer trust?
- Do you have any paper records or third-party backups that could be used to recover data?
- Was only publicly available information compromised, or was sensitive customer data exposed?
- Is the ransom demand affordable, or would paying it cause significant financial hardship?
- Certain industries have regulations regarding data security and breach notification. A ransomware attack could lead to legal repercussions.
2. If you had to reformat your entire system and replace some hardware to return to normal operation, what would be the consequences?
The scope of the attack will also affect its reach and potential devastation to your operations. Ask yourself:
- Would lost productivity or replacement costs cause significant financial strain?
- Were only non-critical systems affected, or were core functions impacted?
- How long would it take to get critical systems back online? Can you operate without them?
- How quickly can you reinstall essential software and operating systems?
- Does your cyber insurance policy cover ransomware attacks and data recovery costs?
3. Do you have security insurance and other prevention measures to mitigate the impact of cyberattacks?
Prevention is the first line of defense against cyberattacks, with mitigation being a crucial second. Does your insurance cover ransomware? And did you know you can reduce the premiums by implementing some well-known industry standard solutions? Things to consider:
- How effective are your current cybersecurity measures in preventing future attacks?
- Do you have a robust backup strategy with backups stored securely offline?
- Have your employees been trained on cybersecurity best practices to avoid phishing and malware attacks?
- Do you have a documented disaster recovery plan that outlines steps for recovering from an attack?
An IT/OT Assessment: Getting Started by Protecting the OT Network
Protecting an OT network begins with fully understanding the current network topology as well as the layout and credentials of the devices that currently communicate on it. Without understanding the morphology – technological and physical – of your entire network, you can’t ensure that all gaps and weak spots are identified.
An IT/OT assessment performed by experienced system integrators will provide this detailed inventory of the current state of a company’s network and devices. Vulnerabilities will be identified so defensive and offensive approaches to dealing with cyber threats can then be considered.
Continual Verification: The Basics of the Zero Trust Approach to Security
To combat the ever-increasing complexity of cyberattacks, a multi-pronged, offensive and defensive approach must be taken. The “Zero Trust” strategy has been around for a while but has recently gained attention by OT security providers looking to implement the approach to their networks.
Zero Trust is a different, nearly inverse approach than that which is normally implemented within an OT network, which assumes a “safe zone” and primarily defends that zone at its perimeter. In contrast, Zero Trust is a cybersecurity strategy based on complete skepticism of everything all the time.
In a zero trust approach to security automation, there is:
- No initial or continual trust for any device attempting to access the OT Network.
- Full identification and credentialing on a continual basis.
- Continual traffic monitoring, limited access, and no safe perimeter is assumed.
- A collection of network components and software solutions, each doing their own task that collectively keeps the network secure.
To begin the process of protecting an OT network, organizations should consider conducting an IT/OT assessment to identify vulnerabilities and then consider the process of implementing the Zero Trust OT network architecture. E Tech Group can perform this initial assessment and support you through mitigation, remediation and prevention. And as a Main Automation Partner, we can protect the integrity of your cybersecurity measures long-term, updating and reinforcing them as needed.
The second part of this blog series, “Zero Trust Ensures Plant Resilience During a Cyberattack”, will discuss the specific devices needed to adequately implement architecture that ensures the OT network is effectively monitored and defended from cyberattacks.
Begin Your Journey to Industry 4.0
Download our Beginner’s Guide to IT/OT Assessments to gain an understanding of what an IT/OT Assessment is, its benefits, and how to get started today.