The Project: Create a Custom Control Panel Design for an R&D Lab
AA leading manufacturer of liquid-cooled server racks for data centers sought to develop a test assembly for donation to a University Research and Development Data Center. This facility would use the assembly to test liquid-cooled equipment and refine designs for greater efficiency.
The control panel design would have to allow seamless control of pumps, fans, and temperature sensors, with transparency into all automated processes, the data from which would provide insight into how the lab could improve equipment design. The client reached out to E Tech Group for our ability to design and fabricate custom control panels for any automation application.
The Challenge(s): All Sorts of Project Constraints
The design of the control panel wasn’t the only unique factor in this project. The server rack manufacturer undertook this project as an endowment to the university, so project resources and timeline had to be handled carefully. Key challenges included:
- Limited Budget and Aggressive Timeline: The client required a cost-effective solution that could be delivered promptly.
- Design Constraints: The assembly needed to fit within a server rack with a 3U clearance or less, ensuring portability between racks.
Additionally, the project demanded precise control for testing, which necessitated custom engineering expertise.
The Solution: Research & Design the Ideal HMI Solution
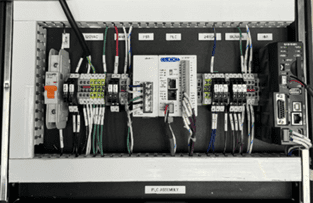
E Tech Group engineered a cutting-edge server rack tray control panel tailored to the client’s stringent requirements. Key elements of the control panel solution included:
Custom Hardware and Software Development:
- Control Panel Design: Built to fit the 3U clearance while remaining portable.
- PLC Programming: Incorporated PID position control for a valve, using pressure sensor feedback for precision testing.
- Headless HMI Integration: Enabled R&D technicians to adjust PID settings via a web browser, ensuring flexibility and ease of use.
Technology Selection:
- Deployed Automation Direct PLC and headless HMI to align with the client’s preferred platform and cost constraints.
Overcoming Challenges:
- Leveraged innovative design strategies to accommodate space and functionality requirements.
- Delivered a fully operational test assembly on time and within budget.
The Results: Supporting the Next Generation of Data Center Automation
The project successfully met all design and operational objectives, earning the client’s trust and opening doors for future collaborations. Notable outcomes included:
- Cost Efficiency: Delivered a robust solution within the client’s budget.
- Enhanced R&D Capabilities: The University Data Center gained a versatile, user-friendly test assembly, empowering them to optimize liquid-cooled server designs.
- Client Relationship: The project’s success led to additional work opportunities with the client, strengthening their partnership with E Tech Group.
This case exemplifies E Tech Group’s ability to deliver high-value engineering solutions under tight constraints, showcasing our expertise in automation and our commitment to client satisfaction.